 Being Digital, Journey to Digital, Digital, 21st Century Humans, are phrases that are common place in many conversations around business and technology. But what does it mean to be “Digital”. This is a wide subject to cover in a single blog post, so here is an A-Z of Digital to help.
Being Digital, Journey to Digital, Digital, 21st Century Humans, are phrases that are common place in many conversations around business and technology. But what does it mean to be “Digital”. This is a wide subject to cover in a single blog post, so here is an A-Z of Digital to help.
I will break these down in further blog posts going into each subject in more detail.
A – Automation
The manual tasks of today should be the automated tasks of tomorrow, achieved using tools that interface with systems using API’s and commands that join them together to carry out tasks. From turning your heating on using an application to automatically carrying out a set of repetitive tasks to allow other more complex tasks to be undertaken.
B- Blockchain
A blockchain is a distributed database that is used to maintain a continuously growing list of records, called blocks. Each block contains a timestamp and a link to a previous block. A blockchain is typically managed by a peer-to-peer network collectively adhering to a protocol for validating new blocks. By design, blockchains are inherently resistant to modification of the data. (Wikipedia).
C – Cobots
Cobots are Robots that are adapted and programmed to work and interact with humans in various tasks and levels of activity. Imagine you’re working buddy is a cobot that can perform tasks hand in hand with you, take over if you need to do something else, increase its speed of completing the tasks, then sense your return and slow to the speed your working at.
D – Digital
“Digital” is an umbrella word that covers many different topics. There are many definitions available, but for me this is about how we unlock the capabilities available today and use them to better our lives and society. From a business view this is about growth and transforming through processes and technology. Being Digital is not necessarily about having the latest gadgets, but more around how you are using them and what you do.
E – Evolution
Evolution covers the advancements and new technologies that are being discovered and created every day. There are lots of new ideas and products coming out of sites such as crowdfunding and crowdsourcing sites, some work however some do fail. These sites are worth tracking to see what developments are coming around the corner.
F – Fitness Trackers
Fitness trackers are probably one of the most common wearable that is available today and have been around for a number of years. Trackers have developed to include a wide range of functionality including heart rate, blood pressure, location, altitude making the data useful to the health and medical industries to understand how we lead our lives.
G – Geolocation
Geolocation ties into a lot of the items in this list and provides a basis for providing location and tracking capabilities for devices and applications. It is also used to locate and pinpoint where users are. Some services cannot be consumed these days without agreeing to having this information shared with a site. The most common type of application in wide use is a Sat Nav.
H – Hybrid
Hybrid is used as a term to describe a mix of public and private services, such as a Hybrid Cloud where services can be mixed between traditional on premise/data centre services and cloud services, providing some control or orchestration layer across both to allow users to consume based on policy or requirements.
I – IoT
IoT (Internet of Things) is where physical things are connected by the internet using embedded sensors, software, networks and electronics. This allows the items to be managed, controlled and reported on. There are many reports estimating the number of IoT devices likely to be connected in the future, these are between 20 and 50 Billion devices by the year 2020.
J – Jacking
Jacking is a term used when you plug into something. Body Jacking is a growing area where the body is being used from generating power through movement to implanting chips to interact with the environment such as open a door or unlock a computer. This also covers Bioables which collect data on your body such as glucose levels using sensors that penetrate into the under the skin.
K – Knowledge
Understanding what is going on in your streams, market places and industries is a big task. Lots of information coming in on a daily basis – drinking from the fire hose, not able to consume it all. Creating your Personal Knowledge Management System will help navigate the sea of information and pick out what is key to your situation and what can be dropped.
L – Legal
With the increasing about of things interacting with our daily lives, the area of Legal and Security play a big part. There are a number of important questions to ask – Where is your data being stored and who actually owns it. Is your data secure and have you implemented all the right controls? What does Legistlation such as GDPR mean to you?
M – Machine Learning
Machine Learning (ML) allows a computer to learn and act without being explicitly programmed with that knowledge. An example of Machine Learning Algorithm is a web search engine that brings up a number of results based on your search criteria and shows which could be most relevant to what you are looking for.
N – Networks
Networks and connectivity form the backbone of the systems in use today. Using a number of different types of network from Cellular (3G, 4G) to traditional networking and futures of 5G and Neural Networks speeding up how we create, consume and process data.
O – Organisation
Infrastructure as Code looks at making hardware being able to controlled at a code level, allowing Microservices and the ability to consume capability quickly. The next stage is the Organisation as Code. A great example of an Organsation as Code is Uber, building services and the supporting organisation in the cloud that allows it to be consumed anywhere and the drivers to login and become part of that organistation for the period that they are employed.
P – Programming
Everyone should learn to code. Learning to code (Programme) in a language like Scratch, Python, Java, C, etc. The ability to code will allow someone to understand how they can automate a task using tools and API’s.
Q – Quantum Computing
A computer which makes use of the quantum states of subatomic particles to store information (Dictionary). Quantum Computers are being developed with the ability to compute data at an exponential rate allowing for quick computing of complex data.
R – Robots
The vision of Robots has been around in early Science Fiction and are very much a reality today. From an automated manufacturing plant to a robot to help you shop and carry out tasks. The field of robotics is advancing bring in Artificial Intelligence and Machine Learning to boost their capabilities and means to learn, self-think and complete tasks.
S – Social
Being social is not just around how you use the tools and what you tweet, but also what you don’t say and being Social Media savvy on your communications. There is a large number of social tools available with some well-known such as Twitter, Facebook and Linked in to those not so. It is also about how you organise your life with these tools and use them for productivity and security.
T – Twenty First Century Digital
The term 21st Century Digital applies to the current century and how you are using Digital to better your organisation and yourself. The LEF (Leading Edge Forum) has information that covers these two topics as the 21st Century Organisation and 21st Century Human.
U – Usability
The usability and user experience of devices is key. Understandoing and being able to interact with devices is important. If a someone can’t use the application or device they may start looking for an alternative that they can use.
V – Visionables
Visionables moves the wearables market to technologies that help enhance our experiences through what we see. This covers things like Smart Glasses, Virtual Reality, Augmented Reality and Mixed Reality.
W – Wearables
The field of wearables is expanding with more ways to attach sensors and record data about our daily lives. This typically covers anything that you can wear or attach to your body and in the main interfaces with a mobile to be the central data point, although many devices operate separately and can transmit data themselves.
X – Xperience
Xperience covers how we use these technologies and advancements to shape our lives and the effects that they have on them. How we have moved from the days of the first computer to today’s wearable and interactive society.
Y – Yottabyte
Yottabyte is a term used to define an amount of storage. The prefix yotta indicates multiplication by the eighth power of 1000 or 1024 (Wikipedia). The amount of storage used today is seeing huge daily growth with systems currently using petabytes of data. The trends will increase the amount of storage needed to hold data.
Z – Zabeta
Zabeta is a noun meaning Tarrif or Tax. As we move to a more automated society there is a view point that automation and robots should be Taxed.
This is my current A to Z and some of the entries may be different in your version. Do you agree with the list? Whats in your “A to Z of Digital”?
 With the typical home now being enticed into the world of the “Smart Home”, IoT (Internet of Things) and Connected Everything the number of hubs being offered with each service is growing.
With the typical home now being enticed into the world of the “Smart Home”, IoT (Internet of Things) and Connected Everything the number of hubs being offered with each service is growing.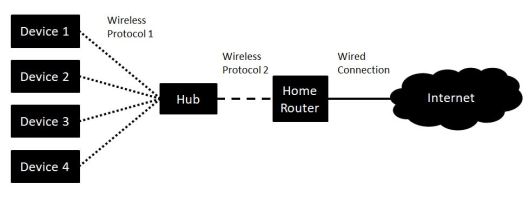


 Being Digital, Journey to Digital, Digital, 21st Century Humans, are phrases that are common place in many conversations around business and technology. But what does it mean to be “Digital”. This is a wide subject to cover in a single blog post, so here is an A-Z of Digital to help.
Being Digital, Journey to Digital, Digital, 21st Century Humans, are phrases that are common place in many conversations around business and technology. But what does it mean to be “Digital”. This is a wide subject to cover in a single blog post, so here is an A-Z of Digital to help. Have you every gone to the app store and just installed something on there because it looks good and something you want to look at, or purchased a product and then installed the app without thinking or checking it out first? Lots of people do, but do they really know what is going on under the covers?
Have you every gone to the app store and just installed something on there because it looks good and something you want to look at, or purchased a product and then installed the app without thinking or checking it out first? Lots of people do, but do they really know what is going on under the covers?
 There are many and apps available to help us automate basic tasks on our mobiles and computing devices. When choosing these tools, we often read reviews and then download the app, run and set up, then let it run its tasks accepting that it will carry out our requirements. But what happens when there is an issue.
There are many and apps available to help us automate basic tasks on our mobiles and computing devices. When choosing these tools, we often read reviews and then download the app, run and set up, then let it run its tasks accepting that it will carry out our requirements. But what happens when there is an issue. There are lots of voice activated tools and services now available from software on your PC and in your car to physical hardware you can place around your home. These devices are becoming everyday occurrences, “Alexa, whats the weather”, “Siri, recipe for Chocolate Cake” (too many to list).
There are lots of voice activated tools and services now available from software on your PC and in your car to physical hardware you can place around your home. These devices are becoming everyday occurrences, “Alexa, whats the weather”, “Siri, recipe for Chocolate Cake” (too many to list). Its always great when you get a phone call saying “Hello, I’m calling from Microsoft and we have noticed a problem with your computer”. My inner kid springs to life and its time to string on the scammers.
Its always great when you get a phone call saying “Hello, I’m calling from Microsoft and we have noticed a problem with your computer”. My inner kid springs to life and its time to string on the scammers. Reports from CES 2017 is seeing some great advancements in consumer tech coming out in the journey to digital. Coupled with some recent reports from around the web I have been thinking about the question “How secure is my home in the digital age?”
Reports from CES 2017 is seeing some great advancements in consumer tech coming out in the journey to digital. Coupled with some recent reports from around the web I have been thinking about the question “How secure is my home in the digital age?” The IOT Security Foundation has released
The IOT Security Foundation has released  The use of Social Media Identities, have been used for a while now as an alternative to the usual username and passwords traditionally used.
The use of Social Media Identities, have been used for a while now as an alternative to the usual username and passwords traditionally used. So usual changing of passwords are key to ensure that its not the same as on a list. Typically any logins and passwords for sale will be used/tested on multiple sites by hackers to check if you have used the same password on multiple sites. Good practice should be that you use different passwords on different sites to avoid anyone trying this technique, however the management of such a practice often inhibits this from being done. People may decide to install a password manager to help them navigate the miriad of logins and passwords.
So usual changing of passwords are key to ensure that its not the same as on a list. Typically any logins and passwords for sale will be used/tested on multiple sites by hackers to check if you have used the same password on multiple sites. Good practice should be that you use different passwords on different sites to avoid anyone trying this technique, however the management of such a practice often inhibits this from being done. People may decide to install a password manager to help them navigate the miriad of logins and passwords.