Modern organisations operate within intricate ecosystems comprising applications, processes, data flows, technologies and external partners. Despite this complexity, many organisations still communicate their architecture using simple diagrams often created in Visio, PowerPoint or even hand drawn on paper and whiteboards. While these approaches offer flexibility and speed, they lack the structure and clarity essential for effective collaboration and robust governance at scale.
Limitations of Standard Diagrams
Ad-hoc diagrams are prevalent in many organisations, yet as business environments grow more complex, they introduce significant risks. The key issues include:
- Inconsistent Interpretation: Stakeholders may interpret elements differently, leading to confusion and miscommunication.
- Lack of Structured Layers: There is often no clear distinction between business, application and technology domains unless specifically drawn in or labelled.
- Artistic Licence: There can be many differences in the way different architects draw their diagrams.
- Limited Reusability: Diagrams are difficult to reuse or adapt, resulting in duplicated effort.
- Weak Impact Analysis: The absence of defined relationships makes it challenging to assess the consequences of change.
- Time to Change: Changes often need additional time as objects need to be manually moved around a page and lines redrawn to link these together.
These shortcomings create governance challenges, slow down transformation efforts and can hinder collaboration between teams.
While there will always be a place for these types of diagrams within architecture to address specific use cases, it is essential to adopt a holistic modelling framework or standard for comprehensive and effective enterprise architecture. There are two possible solutions to help.
The Case for ArchiMate
ArchiMate, developed by The Open Group, is a modelling language purpose built for Enterprise Architecture. It establishes a common language for architects, delivery teams and clients.
- Structured Notation: ArchiMate offers clear, layered modelling across business, application and technology domains.
- Multiple Viewpoints: With over twenty standard viewpoints, stakeholders can focus on the aspects most relevant to them.
- Cross-Domain Consistency: ArchiMate ensures traceability from strategy through to execution, supporting alignment across the organisation.
- Industry Alignment: The language integrates with frameworks like TOGAF, making it a natural choice for Enterprise Architecture teams.
By adopting ArchiMate, organisations can model not only their systems, but also how those systems underpin business capabilities, goals and strategic change.
The Case for UML
While ArchiMate addresses strategic and enterprise-level concerns, UML (Unified Modelling Language) specialises in detailed system and software design. UML is widely used to create precise models of software architectures, components, interfaces and behaviours.
- Detailed Modelling: UML excels at capturing the intricacies of software systems, including classes and dynamic behaviours.
- Clear Communication: UML diagrams provide developers and architects with a shared understanding of system structures and interactions.
- Low-Level Design: UML’s strength lies in modelling dynamic behaviour and implementation details, complementing ArchiMate’s high-level abstraction.
For solution architects, UML is vital to ensuring rigorous design and a smooth handover to engineering teams.
Synergy: Using ArchiMate and UML Together
A combined approach leverages the strengths of both languages. ArchiMate provides the strategic, enterprise-wide context, while UML delivers the technical detail necessary for implementation. This synergy ensures a seamless transition from strategy to solution, bridging the gap between business vision and technology execution.
Business Benefits: Improved Communication, Risk Reduction and Scalability
Structured modelling languages offer clear advantages over informal diagrams:
- Unambiguous Meaning: Every element and relationship has a defined semantic, removing ambiguity.
- Effective Impact Analysis: Dependencies and consequences of change are visible early, supporting informed decision-making.
- Governance and Compliance: Models support stronger oversight, risk management and regulatory compliance.
- Scalability: Modular, reusable models can be shared and versioned across distributed teams and geographies.
These benefits help organisations reduce project risks, improve alignment and enable more efficient collaboration.
Tool Ecosystem: Supporting Modelling Quality
Modern modelling tools further enhance the value of ArchiMate and UML. Platforms such as Bizzdesign, Archi and Sparx EA provide:
- Native Support: Tools offer built-in support for ArchiMate and UML streamlining modelling processes.
- Integrated Repositories: Solutions like Sparx EA enable modelling across abstraction levels within a single environment.
- Automated Consistency Checks: These tools help enforce standards and minimise human error.
- Accessibility: Open-source options such as Archi make structured modelling accessible to all teams, regardless of licensing constraints.
This ecosystem of tools elevates modelling quality, maintains consistency and supports collaborative workflows.
Enabling Digital Transformation
Structured modelling languages are indispensable during periods of strategic transformation, cloud migration, and organisational modernisation. ArchiMate, in particular enables organisations to:
- Reveal how capabilities, applications, data flows and infrastructure interrelate.
- Align architecture decisions with business drivers, goals and expected outcomes.
- Clarify large-scale change by unifying multiple perspectives within a single coherent model.
Transformation initiatives are far more likely to succeed when teams use structured models to guide and communicate change.
Summary Table: Standard Diagrams vs. ArchiMate/UML
| Challenge with Standard Diagrams | Benefit with ArchiMate / UML |
| No semantics | Formal meaning and consistency |
| Inconsistent visuals | Standardised notation |
| Hard to scale | Reusable patterns and multi-stakeholder views |
| Limited impact analysis | Relationship driven modelling |
| No clear linkage from strategy to design | ArchiMate → strategy & enterprise UML → detailed system design |
| Tooling limited to drawing | Tools support modelling, versioning, analysis |
Conclusion
Standard diagrams may suffice for informal, short-term communication, but they fall short in enterprise architecture, where clarity, consistency and strategic alignment are crucial. Structured modelling languages such as ArchiMate and UML form the foundation for modelling complex systems, reducing risk, and ensuring accurate communication between business and IT teams.
Organisations should invest in modelling guilds, shared training and cross-team practices to encourage adoption. Moving to formal modelling languages is not just a technical upgrade—it represents a strategic evolution, essential for digital-first enterprises.
Business and IT leaders should:
- Establish an Enterprise Architecture Office.
- Review current architecture practices and identify areas that would benefit from structured modelling.
- Invest in training and tools that support ArchiMate and UML.
- Promote collaboration across teams using shared modelling standards.
- Leverage modelling languages to support transformation, governance and compliance initiatives.
By adopting these modelling languages organisations can unlock greater strategic value, drive successful digital transformation and ensure long-term resilience in an ever-evolving business landscape.
Sources/References
NCSC Annual Review 2025 – Cyber Resilience & EA Modelling
Source: Building Cyber Resilience: Enterprise Architecture and ArchiMate for Strategic Security
https://maxhemingway.com/2025/10/14/building-cyber-resilience-enterprise-architecture-and-archimate-for-strategic-security/
Using ArchiMate with UML – Framework Integration Guide
Source: Using the ArchiMate Language with UML
https://archimate.visual-paradigm.com/2025/02/18/using-the-archimate-language-with-uml-a-comprehensive-guide/
Why ArchiMate is the Modelling Standard for Enterprise Architecture
Source: EA Learning – Why ArchiMate is the modelling language for enterprise architects
https://www.ealearning.com/blog/why-archimate-is-the-modelling-language-for-enterprise-architects/
UML and ArchiMate Coexistence in Sparx EA
Source: UML vs ArchiMate: When to Use What, and How They Coexist in Sparx EA
https://www.nilus.be/blog_posts/uml_vs_archimate_in_sparx.html

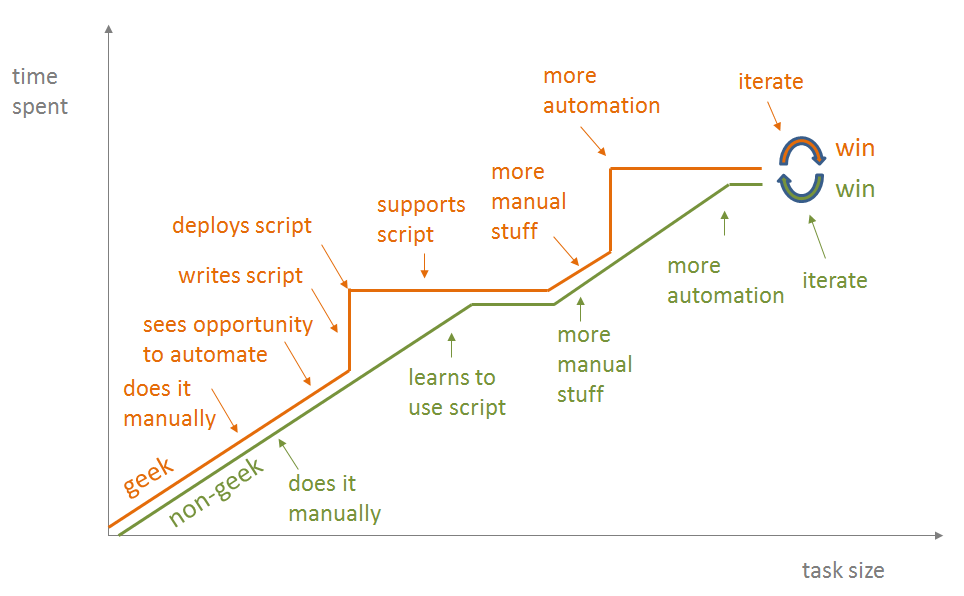
 There are lots of Automation tools available to people and businesses today to automate tasks that are carried out in a manual way. The pace at which this is happening is varying based on
There are lots of Automation tools available to people and businesses today to automate tasks that are carried out in a manual way. The pace at which this is happening is varying based on

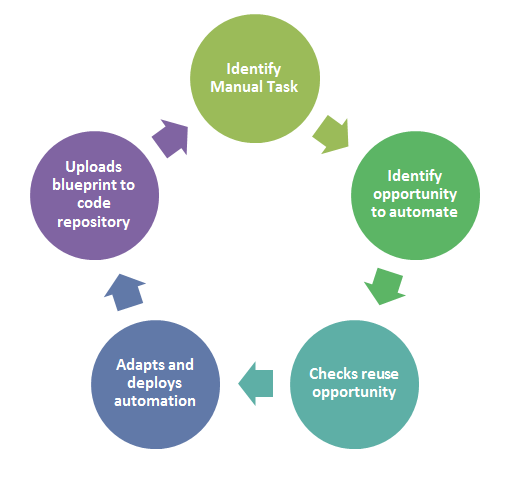
 Being an Architect
Being an Architect The next area in my series on
The next area in my series on